In the world of Android APKs, even after compilation and obfuscation, apps often carry hidden fingerprints—metadata, forensic tags, build traces—that studios and security teams can use to trace leaks, unauthorized builds, or piracy sources. In this article, we’ll peel back the layers on how that works in 2025, what tools and techniques are used, what limitations exist, and what APK developers should know.
Why Fingerprint an APK at Build Time?
Let’s start with the “why.” If you’re distributing a paid or pre-release APK, leaks hurt your revenue and your control. If someone leaks a build, studios want to know:
- Which user or internal tester the build came from
- Whether this build was tampered with
- Which internal version / date the leak corresponds to
By embedding build metadata or forensic tags, studios can trace leaks back to origin, even if the APK is re-distributed or renamed.
What Kinds of Metadata & Forensic Tags Are Used
Here are some of the common traces and forensic methods developers or forensic analysts use:
1. Build timestamps & file timestamps
Each file inside an APK (DEX, resources, assets, etc.) has its own timestamp metadata. By comparing file timestamps across builds, one can infer which build version or branch produced the APK. Tools like GDA (Android reversing / forensic) allow sorting APK internal files by timestamp to trace origin.
2. Embedded identifiers and tags (UIDs, build codes)
Some builds include hidden identifiers—unique IDs, build version codes, tester UIDs, or hashed tokens—inside resource files or in code (strings). Even if minified or obfuscated, those tags (if consistent) help link a leaked APK back to, say, a specific tester batch or internal environment.
3. Silent watermarking or code watermarking
Instead of visual watermarking (for video), developers may insert small bits of code, paths, unreachable methods, or no-op instructions that vary by build. These act as “silent watermarks.” If someone disassembles the APK, the watermark reveals the build origin. This is a software analog to forensic watermarking.
4. Component / resource variants
Sometimes compiled variants differ: debug logging enabled or disabled, alternate resource qualifiers, or extra permissions enabled in internal builds. Those differences can show that an APK came from an internal or staging build vs public. Analysts often compare build signatures, resource trees, or manifest flags.
5. Log / telemetry identifiers
At runtime, an app might report telemetry (error logs, crash IDs) tagged with build metadata (device ID + build tag). If a leaked app connects to official servers, servers might log the build tag, making attribution possible.
Tools & Techniques in APK Forensics
Here are some real tools and methods used in analyzing APKs and extracting forensic metadata.
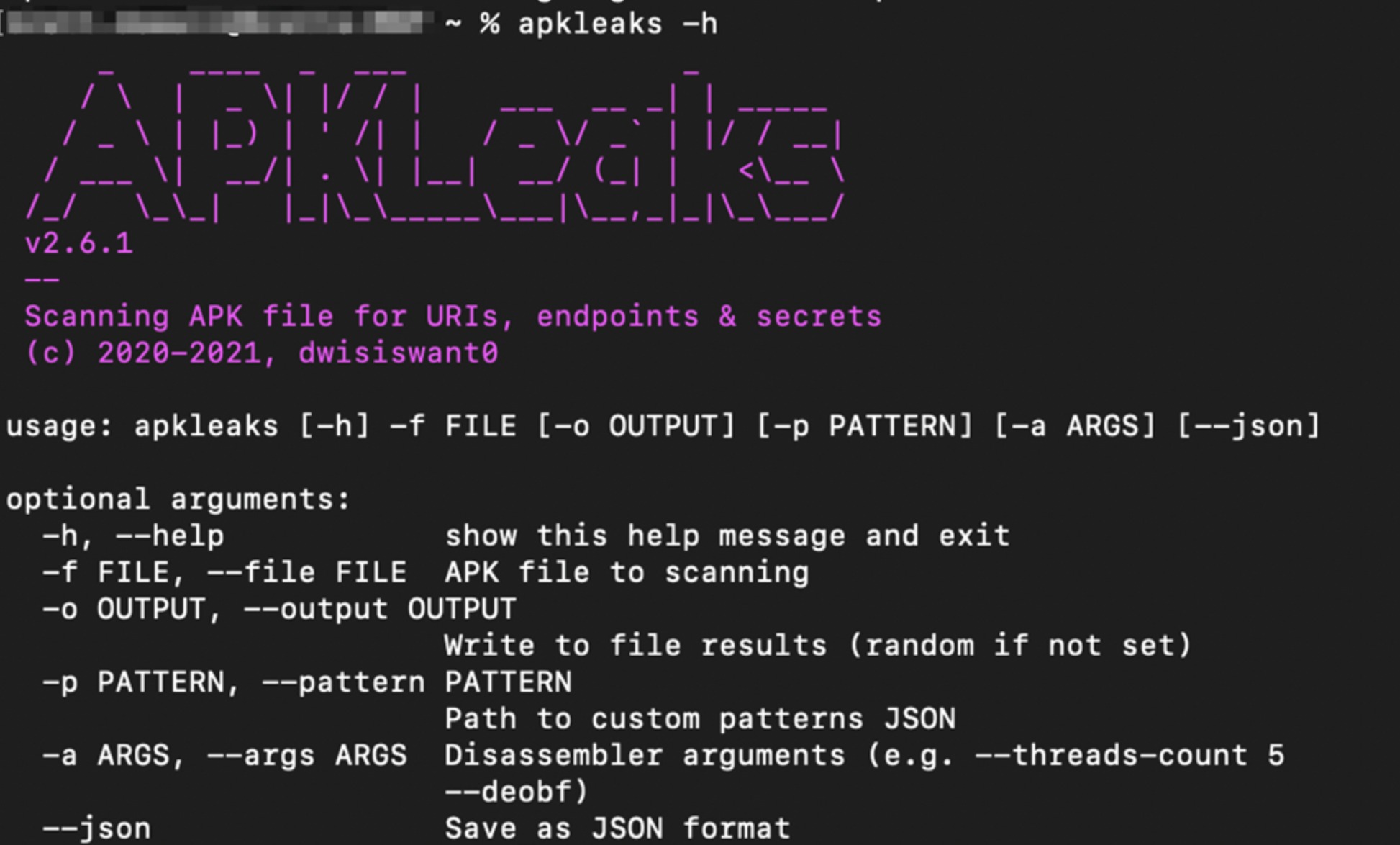
- APKLeaks
An open-source tool that scans APK files for URIs, endpoints, secrets, and embedded strings. Good for discovering endpoints, API keys, and potentially build-specific identifiers. - Static forensics frameworks
Research tools like Fordroid automate static analysis, build control-flow and data dependency graphs, and help locate where data is stored or tagged. Useful in forensic investigations. - Reverse engineering / resource inspection
Using decompilers (e.g. jadx), reverse engineers inspect classes, resource files, manifest, and saved JSONs looking for metadata tags. In GDA reversing tools, one approach is to search for file original timestamps or markers across APK files. - APK quick forensics (apkqf)
An Android app intended for forensic data collection from a device, such as installed packages, build info, system logs. While not directly build watermarking, it helps in gathering metadata from a running Android environment.
How Studios Embed Forensic Tags During Build
Here’s a simplified workflow many development teams might use:
- Generate a unique build identifier (e.g. GUID or hash) per build pipeline run.
- Inject the identifier into resource files, assets, or a hidden class (e.g. com.company.BuildInfo.LEAK_TAG).
- Mix watermark code: insert no-ops, dummy methods, or subtle bytecode differences using build scripts, so every build is slightly distinct.
- Stamp file timestamps consistently (or intentionally vary them) so forensic comparison works.
- Log build tags in telemetry / crash reporting servers, so if the leaked app ever phones home, logs tie back to build tag.
Over time, if a build leaks, you can compare its watermark, timestamps, and identifiers against your build records to trace who had access to that build.
Real-World Examples & Case Snippets
While studios rarely publicly admit using forensic tagging, security researchers often uncover clues:
- Some pentest reports show that leaked internal builds carry hidden resource names or version codes that link back to the studio’s internal CI system.
- Tools like APKLeaks are widely used by security auditors to find suspicious strings or build paths inside APKs.
- In the Android forensics literature, scholars use static analysis to trace code paths, dependencies, and metadata to identify where data or identifiers are stored in the APK. Fordroid, for example, does inter-component static analysis, data tainting, and dependency graphs.
Best Practices for APK Developers & Teams
If you manage APKs or are building apps that require leak resistance, here are prudent practices:
- Use build watermarking only in internal/test branches, not in public (release) versions.
- Keep a build tag history (tag → build metadata) securely in CI logs.
- Obfuscate watermark code / tags so they’re not easily spotted or stripped.
- Monitor your app’s distribution: scan mirrored APKs or public releases using tools like APKLeaks to see if any build tags leak.
- Use secure telemetry: when your app reports crashes or analytics, include your build tag (if ethically and legally allowed), so you can tie execution to build origin.
- Consider combining with other protections, such as signature verification, runtime integrity checks, and server-side validation.
Summary & Final Thoughts
APK build metadata and forensic tags are a subtle but powerful defense for studios trying to guard against leaks and piracy. Even after obfuscation, differences in timestamps, embedded build identifiers, watermark code, or variant features can all serve as fingerprints. Tools like APKLeaks, static forensics frameworks, and reverse engineering help security teams trace leaks back to their origin.
That said, tagging isn’t foolproof—attackers may strip metadata or repack the APK. The key is combining watermarking with secure telemetry and vigilant monitoring. For APK users, knowing these techniques exist helps you understand why some leaks get traced and why internal builds often differ subtly from public ones.